Brute Force IP/Login Restrictions
If your website uses s2Member for membership functionality then you have additional options for adjusting log-in security. To reach these extra security settings you'll click "Restriction Options" under the s2Member menu item in the admin panel. Once you're here click on the "Brute Force IP/Login Restrictions" accordion and you'll be able to select login restrictions from the "Maximum Failed Login Attempts" dropdown. By default this is set to 5 attempts with a 30-minute ban, but you can increase the login attempts up to 100 or completely remove login restrictions. Once you've made changes to the settings on this page you should click the "Save All Changes" button at the bottom of the page.
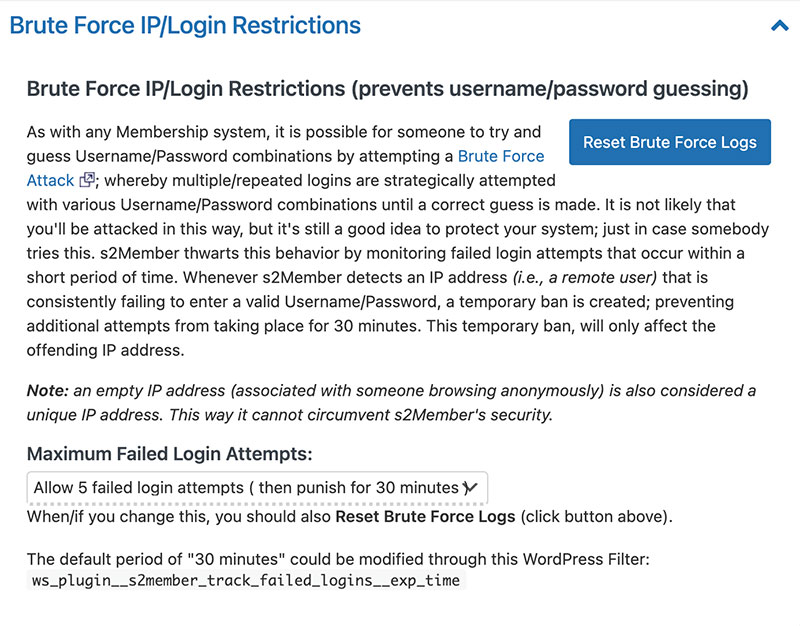
Unique IP Access Restrictions
In addition to brute force protection, s2Member also provides protection against users logging in on multiple devices by restricting the number of unique IP addresses a user can log into the website from during a specified period of time. This setting is located in the accordion section directly under the previous setting on the Restriction Options page of s2Member. There are two dropdowns that you can adjust, the first being the number of unique IP addresses a user can log in from over a 30-day period, from 1 to 100, or the default setting of infinite. The other setting you can adjust is the ban period for users exhausting their allotted unique IP addresses which is from a paltry 5 minutes to the extreme 1-year ban.
Something to keep in mind while making adjustments to these settings is that many users do use multiple devices or access your website from multiple IPs without thinking about it. Limiting the number of unique IP addresses a user can login with can cause problems for this users and result in an erroneous ban. This setting mainly works as a method of preventing users from sharing their login information and giving other users free access to your potentially paid content and is best used in conjunction with the limiting Simultaneous Login Restrictions settings in the next section.
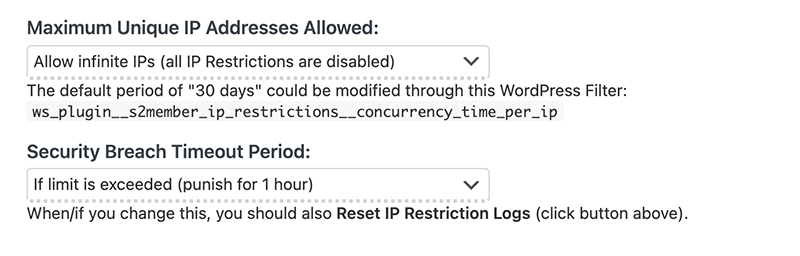
Simultaneous Login Restrictions
The last section you can tweak, located right below "Unique IP Access Restriction", is the "Simultaneous Login Restrictions" accordion. These settings can be used in conjunction with the previous section to prevent users from sharing their login credentials with other users and giving access to your paid and protected content. By default this option is disabled since it is only necessary if your users are exploiting this work-around to gaining access to your protected content.
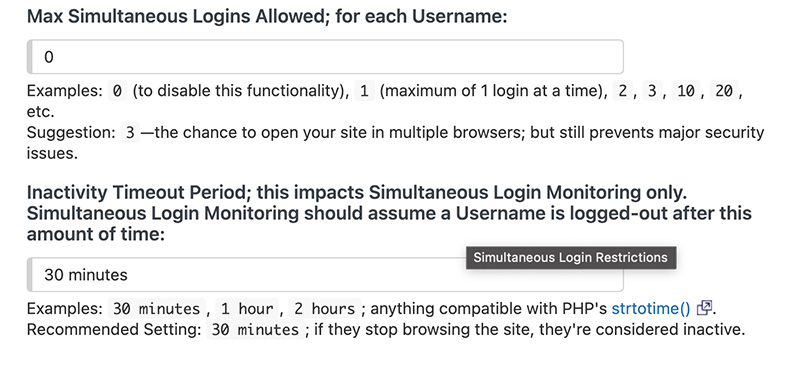
The two options you can enable in this section is the Max Simultaneous Logins Allowed; For Each Username, and Inactivity Timeout. The former allows you to set the number of simultaneous logins anywhere from 0, which disables this feature, to any number you see fit. s2member recommends setting this value to 3 since realistically that's and expected number of devices a user will be accessing your content from, their phone, laptop, and either a tablet or from their place of work. The latter setting, Inactivity Timeout Period, allows you to set the time period in which a user will be automatically logged out due to a user not actively using your website. You can set this value to any length of time, but 30 minutes is the suggested time period. Using the inactivity timeout period is recommended because it decreases the chance that a user will hit the maximum simultaneous login limit in their day-to-day use of your site.
After updating any settings in s2Member you must remember to always click the "save all changes" button at the bottom of the page or your settings will not be saved.
Also, remember that while you may want to protect access to your paid content you need to make the experience for valid users as seamless as possible. There's nothing more frustrating than being erroneously blocked by a website because you logged in on your laptop and then your phone.
If your website uses iThemes then you have additional options for adjusting log-in security and you can find them here.


